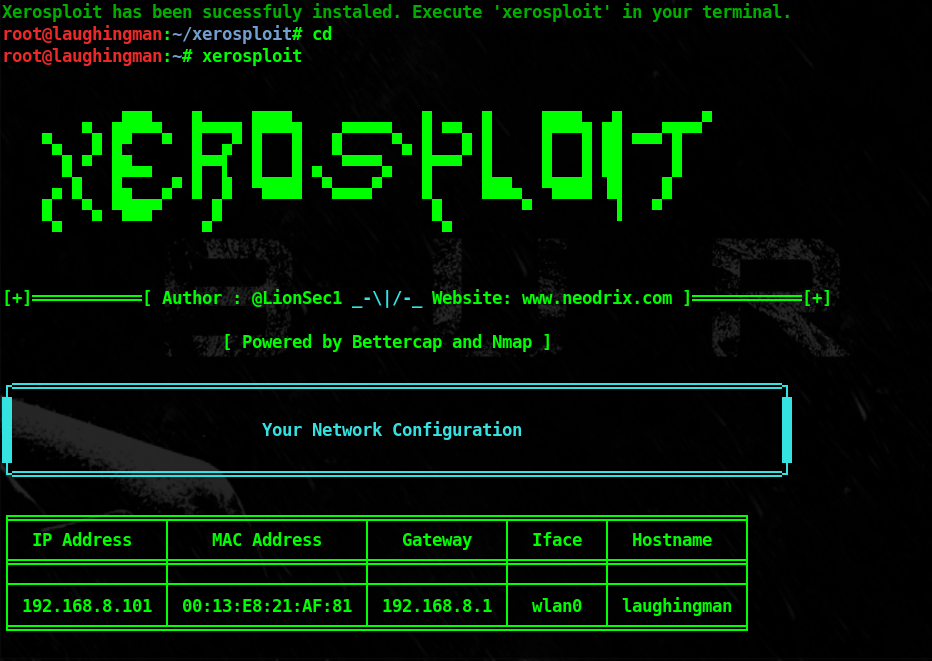
Welcome to hacking a rise i this post we are going to show you how to perform a man in the middle attack with a tool called Xerosploit this tool was designed by LionSec What is Xerosploit Xerosploit is a penetration testing toolkit whose goal is to perform man in the middle attacks for testing …
Introduce Yourself (Example Post)
This is an example post, originally published as part of Blogging University. Enroll in one of our ten programs, and start your blog right. You’re going to publish a post today. Don’t worry about how your blog looks. Don’t worry if you haven’t given it a name yet, or you’re feeling overwhelmed. Just click the …
IntRec – Pack Intelligence and Reconnaissance Package/Bundle installer
Welcome to Hacking a rise in this i am going to show you how to install and use IntRec on any Debian system i am using Kali Linux for this tutorial Whats IntRec IntRec-Pack is a Bash script designed to download, install and deploy several quality OSINT, Recon and Threat Intelligence tools. Due to the …
Continue reading "IntRec – Pack Intelligence and Reconnaissance Package/Bundle installer"
How to use raccoon-scanner
Introduction Hello and welcome to another post and in this one we will be going over raccoon-scanner. This is a high performance offensive security tool that is made for recon and vuln scanning, as they explain it. We'll be going over how to install it and use it + an overview of my experience with …
Beef-xss with html games
welcome to hacking a rise im the laughing man today we are going to show ya ways to trick people clicking your link to hook browsers so this one my fav ways lads i take pride in telling ye how to do this hahaha its funny coz they think they are playing games but really …
How to use netmask
Introduction Hello and welcome to another post, today we are going to be talking about the tool already packed into ParrotSec and Blackarch. Well netmask is an address netmask generation utility as the developer likes to call it, its a great tool in my opinion and today we'll be going over it and what a …
Cewl custom password list
Welcome to hacking a rise i am the laughing man and today im going to show you the basics of Cewl for building custom word lists .. What is Cewl CeWL is a ruby app which spiders a given url to a specified depth, optionally following external links, and returns a list of words which …
How to use Tshark – the brother of Wireshark
Hello everyone~~ This is IRISnoir from Hackingarise. Bringing to you a tutorial. Let's get started. Now, this tutorial's gonna show you about the usage of Tshark Now, a little description: Tshark is the brother of Wireshark. But, Tshark is only compatible on terminal mode while Wireshark can only be used in VNC mode (called wireshark-gtk). …
Continue reading "How to use Tshark – the brother of Wireshark"
How to use traceroute in Termux.
Hello guys~~ This is IRISnoir. And I'll be making this tutorial for yall. This tutorial is about how to traceroute a remote IP through hops. Now, how does this work? You may ask. It traces the given IP by hopping from many devices/IP until it meets its target. This tool is named 'tracepath'. Located at …
How to use dnsmap 0.30
Introduction Hello and welcome to another post, in this one we will go over dnsmap and how it works. I hope you enjoy it!! What is dnsmap? dnsmap was originally released back in 2006 and was inspired by the fictional story “The Thief No One Saw” by Paul Craig, which can be found in the …